iOS 26.1 RC Features: Everything You Need to Know
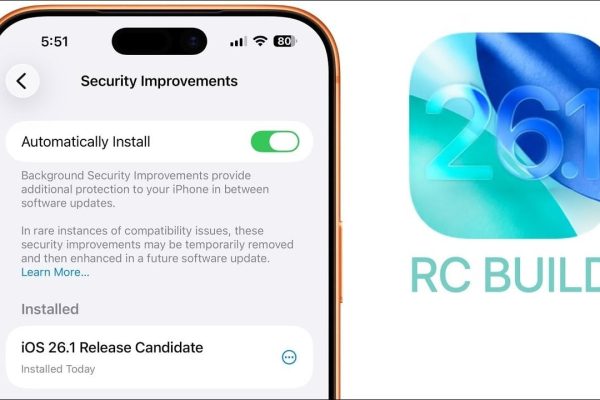
Apple has officially introduced iOS 26.1 Release Candidate (RC), marking a significant step forward in its software development cycle. This update brings a variety of new featuresinterface and performance improvements, all aimed at improving the overall user experience. With updates ranging from visual design improvements has security upgradesiOS 26.1 is designed to provide a refined…