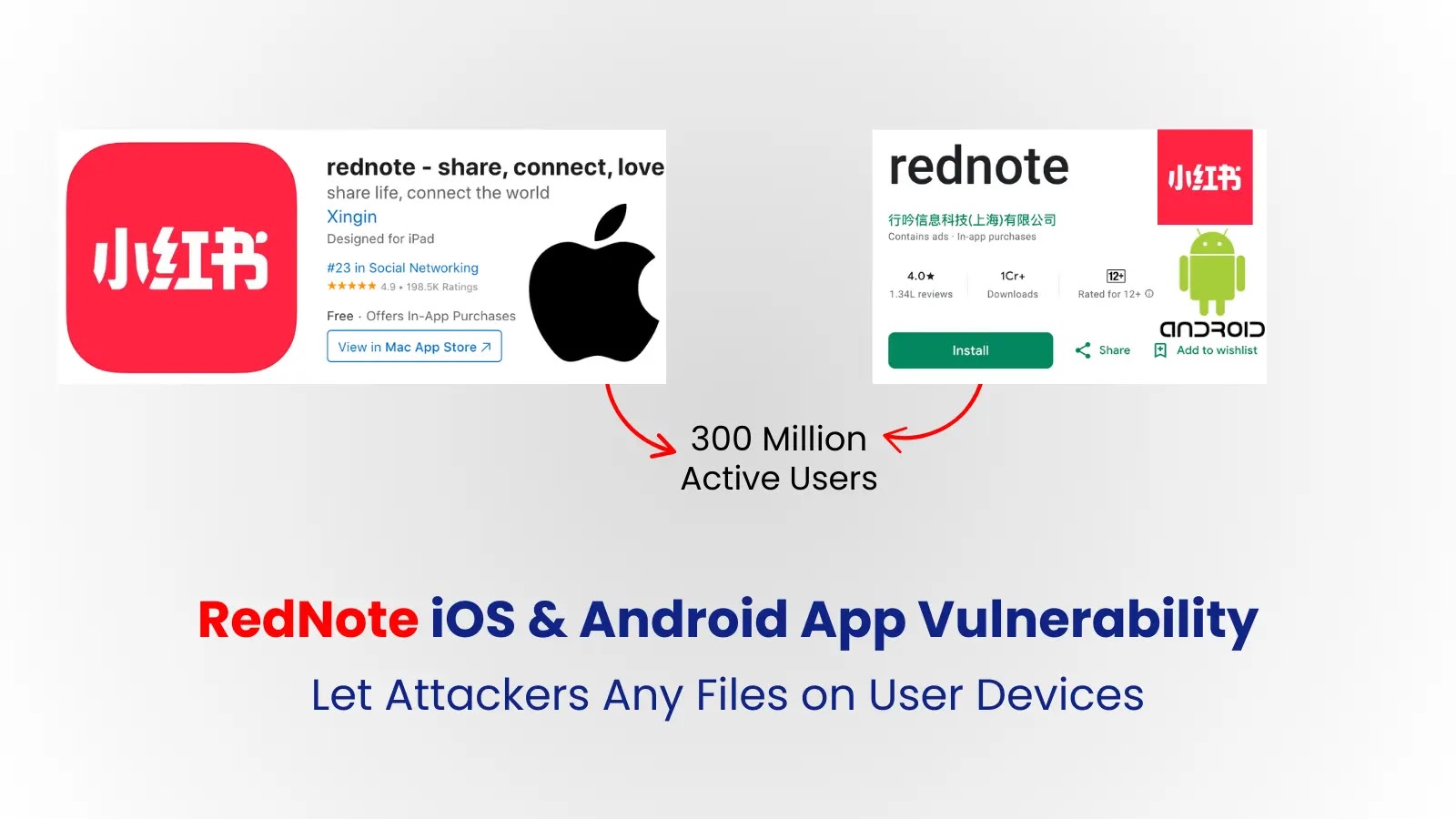
Critical vulnerabilities have been discovered in the popular Chinese Social Media Rednote application (also known as Xiaohongshu), which has more than 300 million active users worldwide.
These safety defects, present in Android and iOS versions, expose user navigation activity, device metadata and even personal files to potential attackers.
The results raise serious concerns about the security of the application, especially since its user base develops in the United States after the ban proposed by Tiktok.
Overview of Rednote vulnerabilities
Unacyed multimedia traffic:
All Rednote’s analyzed versions have recovered images and videos from unacyed HTTP connections.
This allows network listening to monitor user navigation behavior. For example, attackers can determine the videos or images that the user considers by intercepting traffic from the content delivery network (CDN).
File exposure on Android devices:
Some Android versions of Rednote – In particular those downloaded from the official application of the application and the Xiaomi Mi store – continue a vulnerability that allows attackers to access any file that the application has permission to read .
This question stems from an upstream SDK called NextData (or Shumei), which is used for the prevention of fraud. In particular, this defect does not affect the Google Play Store version or iOS versions.
“Network attackers can learn the content of all the files that Rednote has permission to read on the user’s device,” said Citizen Lab researchers
Disclosed peripheral metadata:
All tested versions transmit metadata of sensitive device using low encryption protocols.
Although some versions use TLS (transport the safety of the layer), they fail to validate server certificates, allowing attackers with a man position in the environment (MITM) to intercept data such as the size of The screen, the details of the mobile operators and the specifications of the device.
This vulnerability is attributed to another SDK upstream, Mobtech. The researchers used static and dynamic analysis techniques to discover these vulnerabilities.
Tools like Jadx, Ida Pro and Frida were used for regional code from the application code, while Wirehark and Mitmproxy facilitated the monitoring and handling of network traffic.
An alarming discovery implies the use by the SDK NextData of insecured encryption mechanisms for its “cloud configuration file”.
The SDK uses obsolete encryption algorithms like DES-ECB and AES-CBC with keys coded in hard, which makes trivial so that the attackers decrypt and handle configuration data.
By exploiting this fault, attackers can access files on user devices remotely or execute service denial attacks by injecting malicious regex models into the configuration file.
Likewise, Mobtech SDK requests are encrypted using AES-ECB with static keys but lack validation of appropriate TLS certificate.
This allows attackers to decipher sensitive metadata or to inject useful malicious loads into network requests.
Implications for users
These vulnerabilities present significant risks not only for Chinese users but also for international users, in particular those of countries with advanced surveillance capacities such as the United States and the five nations.
The attackers could exploit these faults to monitor users or compromise their devices on unsuitable networks such as public Wi-Fi.
THE report emphasizes that these problems are not unique to Rednote; Similar vulnerabilities have been observed in other Chinese applications such as Tiktok.
Systemic dependence on proprietary encryption methods or incorrect TLS implementations exacerbates these risks.
Recommendations
For users:
- Avoid using Rednote on unmarked networks.
- Use a confidence VPN service to encrypt network traffic.
- Consider alternative platforms until vulnerabilities are discussed.
For developers:
- Migrate all network communications to HTTPS with a validation of appropriate TLS certificate.
- Replace obsolete encryption algorithms with well -sustained libraries.
- Regularly audit of third -party SDKs for safety compliance.
For regulators:
- Apply stricter data protection standards for applications operating in their jurisdictions.
- Increase the examination of foreign applications giving the data of sensitive user.
This highlights the urgent need for robust encryption practices in popular applications like Rednote.
Until these vulnerabilities are resolved, users must be cautious when using the application, especially in environments subject to surveillance or cyber attacks.
PCI DSS 4.0 and prevention of attacks on the supply chain – Free webinar